When using Azure AD, Conditional Access Policies are used to ensure security is high, logging into applications requires Multi-Factor Authentication. There are features within SAFEQ Cloud meaning you don't need to worry about configuring CA Policies.
When using Azure AD many organisations are using Conditional Access Policies to ensure security is high within their organisation, and logging into applications requires Multi-Factor Authentication.
There are a number of features within SAFEQ Cloud that means we don't need worry about configuring CA Policies, such as using One-Time Passwords for card registration, and SAML configuration for the SAFEQ Cloud Portal.
However, there are some instances that an organisation may want to only use username and password authentication, and are able to configure the CA Policy to whitelist our server IP addresses.
The Authentication micro service would need to be set to the Primary Server for this configuration to work. Primary Servers are load balanced by default, and we publish our outbound IP addresses in Chapter 8 of the Technical Documentation.
IP addresses are subject to change! Please subscribe to service announcements on status.ysoft.cloud to be notified of changes to IP’s.
In order to whitelist our IP addresses, the Azure Administrator needs to add them as a "Trusted Location" in Azure AD - Security - Named Locations. Ensure Mark as trusted location is on.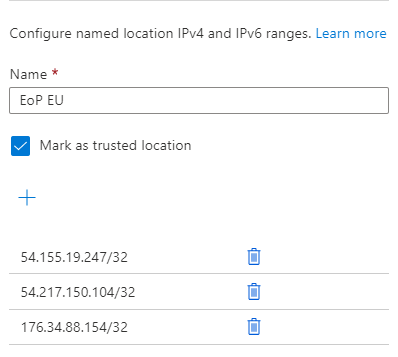
Once the location is configured, then within the Conditional Access Policy itself, you would need to configure the "Conditions".
In this instance Locations need to be selected and "Exclude". 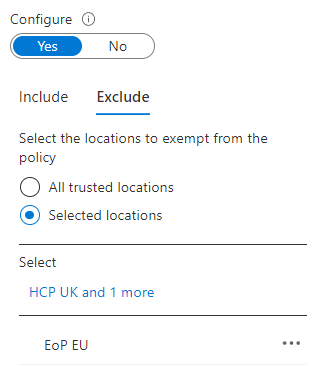
Administrators may exclude all trusted locations, or may need to choose the locations they are excluding.
When this is configured, users should be able to authenticate with username and password.