Print innovations like secure release printing ensure that sensitive and confidential documents are not accidentally or carelessly printed.
Protective data handling practices, such as digital identity verification, secure access management, and secure authentication methods, ensure that companies' sensitive data stays with authorized recipients.
Typically, organizations build a global secure access system to achieve this. Authorized personnel will be asked to enter a password or PIN before releasing a document for printing. Alternatively, you can utilize biometric authentication, such as fingerprint scanning, as part of an identity verification system before printing.
Around 61% of companies in US and Europe experienced print-related data losses in 2023. This underscores the importance of secure release printing as part of print solutions across businesses and organizations globally.
Companies can mitigate print-related risks by implementing an identity verification system like authentication. Secure authentication methods include pull printing, token-based authentication, passwords or pins, biometric identity control, API authentication, and the use of certificates.
Keep reading to learn more about how secure release printing can safeguard data at every stage of your print process, reduce malware exposure, and increase control over your printing infrastructure.
Secure Access Management for Printers
Secure printing ensures that only authorized users can print jobs in their queue and gain access to sensitive information. It ensures that only approved users can access devices and allows administrators to track device usage.
Additionally, the organization can limit or restrict user access depending on the levels of authorization defined. For example, a company may permit guest printing but restrict access to certain devices or functions.
With secure release pull printing, you can prevent unauthorized people from seeing your documents. The system stores your print jobs safely in a special print queue until you release them for printing.
To better understand how secure access management works, let's look at a few key concepts related to print security.
📖 Read on → Print Security and Secure Cloud Services
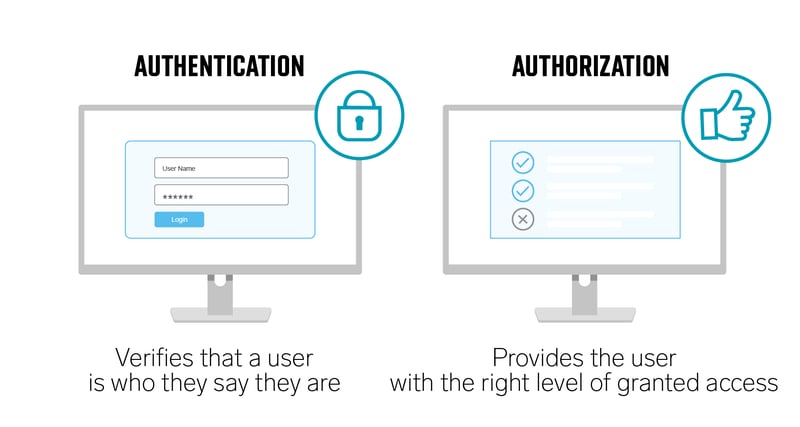
Authentication (AuthN) and Authorization (AuthZ)
Authentication (AuthN) verifies user identities to establish that they are the actual owner of the account associated with a login. This is the first step in any security process. Depending on company policies and security needs, a company may use single sign-on (SSO) or multi-factor authentication (MFA).
Authorization (AuthZ) refers to system security and the resources authenticated users can access. Authorization governs the permitted operations that users can perform within the organization's resources.
- Accessing specific folders in the company file server
- Read-only or read-and-write permissions on a particular server
Authentication and authorization occur in a specific order and are separate steps in the login process. Users first authenticate to verify their identity, then they receive secure access via authorization. People commonly use authorization as a synonym for access control or client privilege. It checks if the user has permitted access based on policies and rules.
Zero-Trust Printing
Zero-trust printing stems from the zero-trust network architecture, a practice that keeps organizations' data secure. Zero-trust printing significantly reduces print-associated risk.
In a nutshell, zero trust is about explicit identity verification (always perform authorization and authentication through every possible data point), least privileged access (don’t give users more access than they need to perform their tasks), and breach assumption (don’t expect safety measures to be inherently sufficient).
📖 Read on → Protect your Data with a Zero-Trust Printing Approach
What Does Hold for Authentication Mean When Printing?
Print hold for authentication means that a printer is waiting for a user's login attempt to match with a pre-authorized user account. If a match fails, it indicates that the server the user is trying to contact is rejecting the user's credentials. In such cases, the requested print queue will not be accessible. This measure works as a safeguard against fraudulent attempts to access information and prevents data breaches from happening.
The “Hold for Authentication” message can be an error message, caused when a user enters incorrect credentials—and the server rejects them. This message is associated with Apple devices. In such a scenario, the job appears to pause in the print queue window with the ‘Hold for Authentication’ message.
Ultimately, the message suggests that the user needs to re-verify their identity. A functioning identity verification system enables organizations to keep their networks secure by permitting only adequately authenticated users access to protected resources.
10 Authentication Methods for Your Print Identity Verification System
Next, we will explore secure authentication methods you can integrate into your print security system. These methods help with the verification of identities across your company.
1. Secure Release Pull Printing
Pull printing enables users to print to a single print queue and collect their print job from any networked printer. The user can only access the queue after they successfully authenticate themselves. The print workflow remains on hold until authentication occurs, i.e., when the user is on location to retrieve their printouts.
📖 Read on → Keep Company Data Protected with Secure Pull Printing
2. Single Sign-On (SSO)
Single sign-on (SSO) is an authentication practice and session that permits users within an organization to log in with a single set of login credentials to any of several related, yet independent, software systems. It enables your users to sign in just once to access all their applications and services.
Users automatically sign in to multiple applications, such as their print software. They can immediately start using the print software to print out any documents they need within their print queue.
3. Two-Factor (2FA) & Multi-Factor Authentication
Multi-factor authentication (MFA) is a multi-step digital identity verification system and login process. The company's authentication mechanism grants access after someone provides two or more pieces of identity evidence.
Many consider multi-factor authentication to be a cornerstone of a strong identity and access management (IAM) policy.
4. Token-Based Authentication/Identity Cards
Token-based authentication allows users to verify their identity with a physical ID attached to an access token. In this scenario, a company will purchase and install card readers (like the YSoft MFX Ultimate Reader, to give you an example) for their multi-function devices.
These readers connect the act of presenting an ID card with appropriate (pre-granted) access to the printer.
5. Username and Password
Authorized users are required to key in their pre-registered username and password to access specific multi-function devices. This type of registration is also known as knowledge-based authentication. As the name implies, this option relies on usernames and passwords or PINs to verify user identities. This is the most popular way to verify identity and is familiar to many companies and users.
Many companies also implement password policies. These policies ensure users change passwords regularly and leverage password complexity (like length, a mix of letters and numbers, and special characters).
6. PIN and User ID
With this option, the company will provide users with a universal PIN and specific user ID to authenticate their identity before accessing print and scan devices, along with other hardware and software solutions
7. Self-Registration
When opting for a self-registration path, users need to log in with a smart card or token before they can access pull printing. Users can sign up for secure printing by scanning a QR code with their mobile devices. A smart card or token generates the QR code.
8. Biometric Authentication
Biometric authentication relies on less easily stolen identity verification credentials. Instead, the system ensures authentication through unique biometric identifiers, like traits or behaviors. These identifiers can be anything from fingerprints, palm prints, facial recognition, iris scans, or voice recognition, to behavioral biometrics.
The authentication method leverages these biometric identifiers to activate access to solutions and functions, like secure print release. Companies do not commonly use this type of authentication for print security. However, it can be a good choice to make company and user data more secure.
According to the European Data Protection Supervisory, there are still negative foreseen impacts with this authentication method. That's why many system and solution providers still focus on other, proven-secure authentication methods.
9. API Authentication with OAuth
An API can enforce authentication (AuthN). OAuth provides authorization (AuthZ) to specific file locations and functions within the API authentication protocols. API authentication is a fundamental way to secure APIs. It enables users and teams to protect sensitive data, build trust, and safeguard the company's resources.
OAuth is the most common specification for API authentication. IT or security teams outsource their user authentication and authorization system to a central identity provider (IdP). The system allows users to securely delegate access to software and other resources without having to share credentials.
In essence, users sign in to the IdP which in turn grants them time-bound permissions in the form of an access token.
10. Certificate-Based Authentication
Lastly, we have certificate-based authentication (CBA). CBA uses a digital cryptography-based certificate to identify a user or device before giving them access to a resource.
This authentication method requires users to prove their identity with a digital certificate that works as a digital passport. The digital passport confirms the user’s identity by confirming that the user owns the private key in question.
Identity & Access Management Protocols (IAM)
Companies undoubtedly have many secure authentication methods and identity verification solutions to choose from and apply to their identity and access management (IAM) protocols.
An Identity and Access Management (IAM) protocol distinctively addresses and ensures the secure transfer of authentication data. Such protocols define security measures, rules, and methods that establish how credentials are created, verified, and canceled. The protocols safeguard information while it travels through networks or between servers.
The protocols help grant users access to applications and systems within an organization
- On-Premises IAM: Active Directory & LDAP
- Cloud IAM: Auth0, Okta, PingID, & More
In any application, an IAM protocol begins with user authentication. Afterward, the administrator defines the locations and services that the user can access and grants authorization. The IAM protocol controls the automated workflow of these authentications and authorizations.
Avoid Credential Theft and Account Takeover
An ATO, or account takeover, is a form of online identity theft. In this type of attack, an attacker steals a user's credentials or personally identifiable information (PII) and poses as a real user.
When an ATO attack is successful, the attacker can easily access a person's personal information. This includes their login details and other secure systems.
To avoid account takeovers and credential theft, organizations should regularly check for compromised credentials as part of their responsibilities. They must also periodically check databases to ensure that existing users' information still matches the registered data.
Login attempts can have rate limits based on the device username and IP address. This helps prevent account takeover because the software will compare known behavior with any unusual behavior. Repeated incorrect login attempts could be an example.
In addition to regular notifications, users should receive immediate alerts when an administrator makes a change to their account. This way, the user can immediately address any potential breach and take the necessary steps to secure their credentials.
FAQs on Secure Authentication and Access
Q1) Why is Secure Authentication Important in Print Security?
Making identity verification mandatory (requiring users to prove their identity) adds a layer of security between adversaries and sensitive data. Secure authentication is crucial to print security because it protects against fraudulent activity, data breaches, careless data handling, and other potential security vulnerabilities.
Q2) How Can Companies Ensure Print Security?
Companies can ensure the use of secure printing by adopting secure authentication systems and global identity and access protocols. A more long-term beneficial route is to leverage a secure cloud print solution. Cloud print software is built on strict security practices, is extremely regulated, and is continually upgraded with enhanced experiences in mind.
Cloud solutions mean IT teams don't have to oversee their print infrastructure. This is because of advanced solutions like cloud-powered secure release printing and authentication methods. Their provider takes care of everything, including security.
Final Points
Print security is non-negotiable.
Secure authentication methods, such as pull printing, multi-factor authentication, or token-based authentication, can help companies ensure that their company and user data remain secure. Secure release printing provides an edge over traditional print with out-of-date security. Only authorized users can command print jobs, reducing errors, data breaches, and personal information getting into the wrong hands.
At Y Soft, we always consider user experience (UX) when discussing print security and identity authentication. When choosing one or more authentication types to implement, companies must consider customer experiences as well as security itself. For instance, friction during authentication can lead to poor employee practices.
With YSoft SAFEQ Cloud, we’ve simplified and consolidated tenants’ authentication settings. A single form combines OpenID Connect (OIDC) and Service Account protocols, making authentication flexible for all users.
This functionality is consistent across Clients, the mobile app, and the web UI, sharing the same login options. As a result, onboarding new users comes with an intuitive and familiar authentication experience
📖 Read on → One Place for Authentication Settings in SAFEQ Cloud
Are you looking for a comprehensive print solution that relieves your team's security pressure? A solution provided by a company with a proactive approach to security? At Y Soft, we upgrade the SAFEQ Cloud platform with new security enhancements and take care of security on your behalf.





